The official Slack documentation states:
By limiting who can post, announcement-only channels are a great way to broadcast information to everyone in Slack. This type of channel becomes read-only to anyone without permission to post. Instead of the message field, members will see a message like this:
Your Workspace Owners have limited who can post to #announcements-global
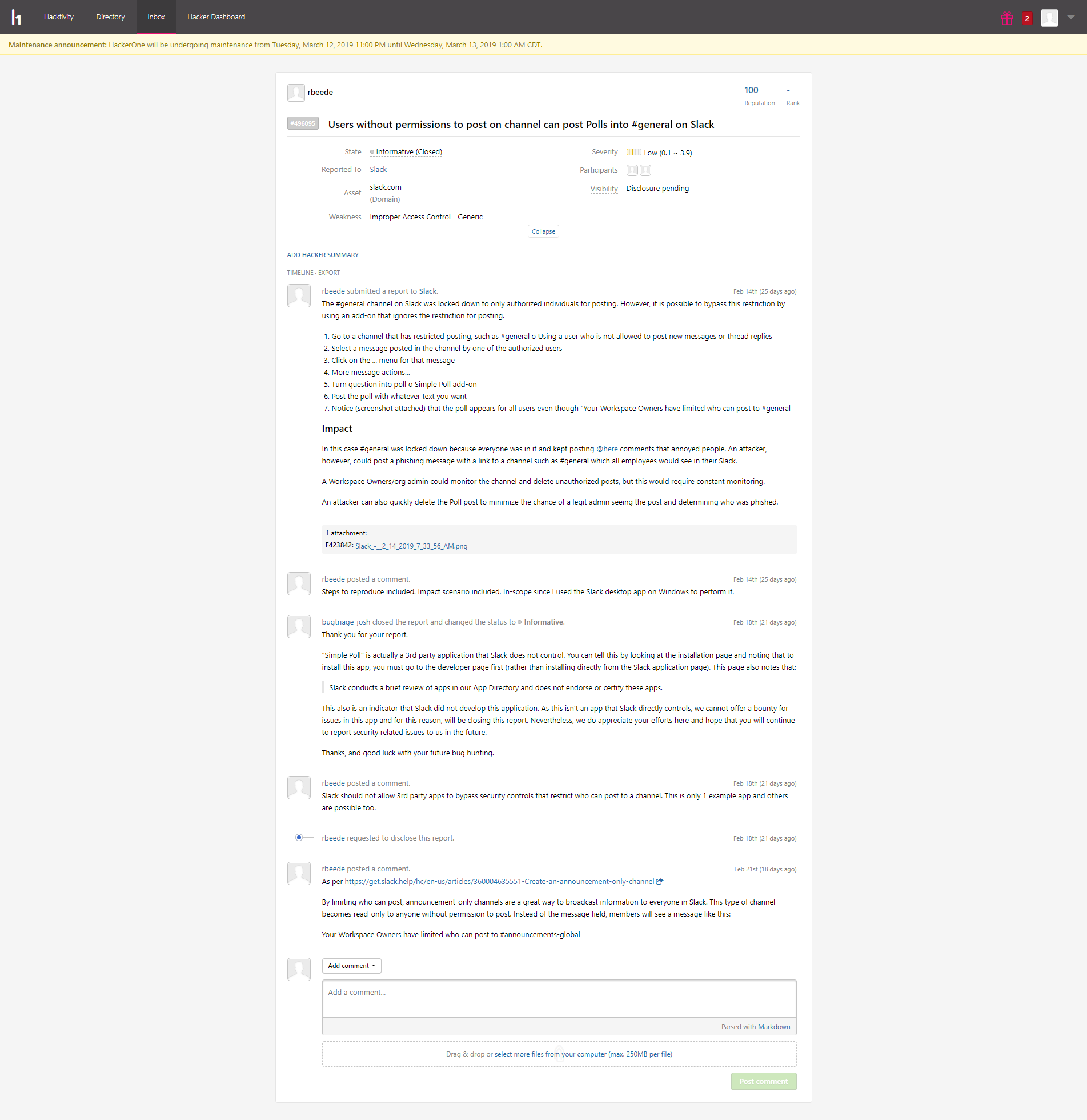
However, I found a way for unauthorized users to bypass this restriction via the use of commonly added third party applications. One example is via the Simple Poll app.
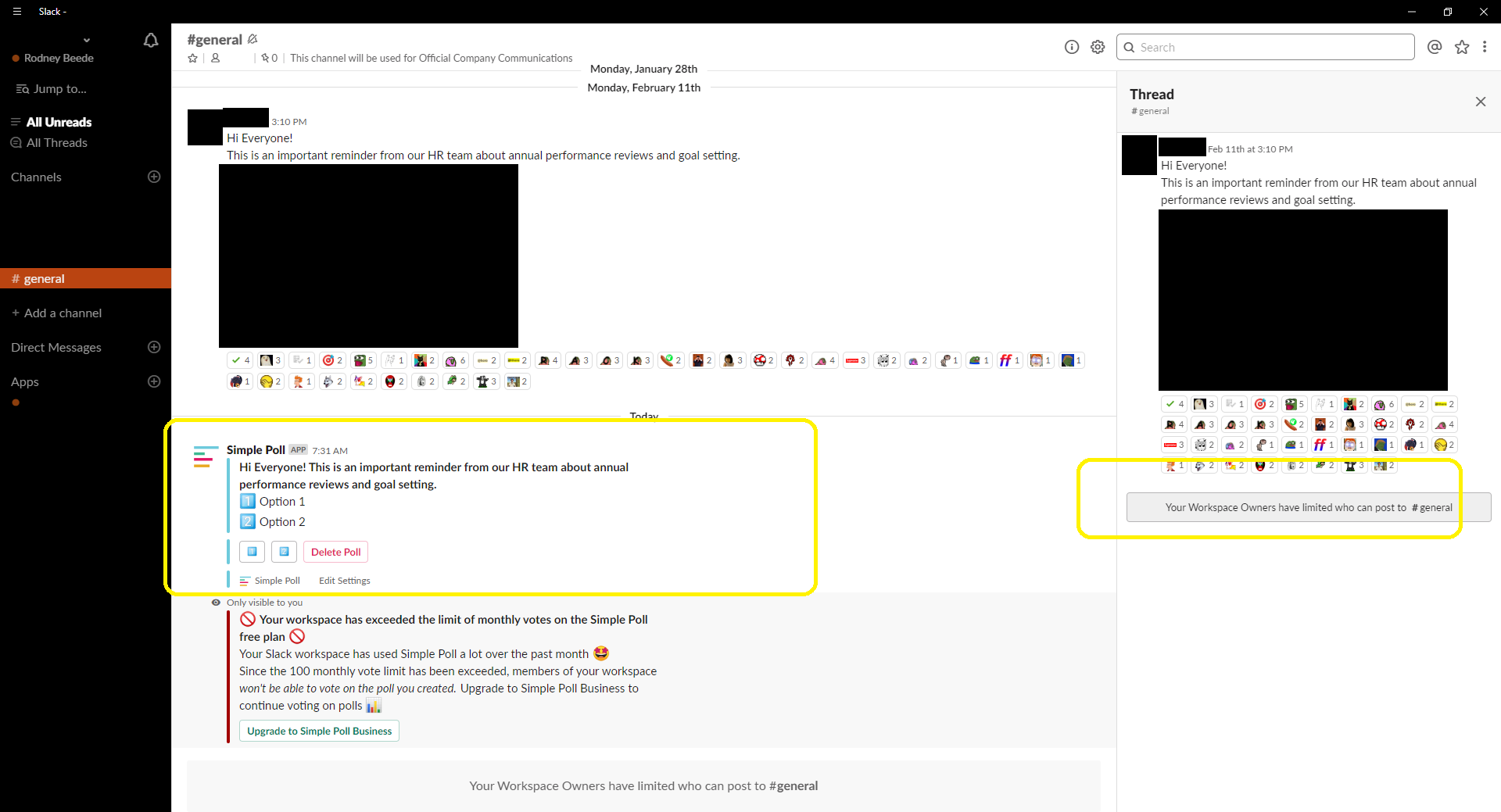
- Go to a channel that has restricted posting, such as #general, using a user who is not allowed to post new messages or thread replies
- Select a message posted in the channel by one of the authorized users
- Click on the ... menu for that message
- More message actions...
- Turn question into poll via Simple Poll add-on
- Post the poll with whatever text you want
- Notice (screenshot attached) that the poll appears for all users even though "Your Workspace Owners have limited who can post to #general
Analysis
This was just one example app. Many other apps could be used as well to do the same. The issue lies in that Slack at its core does not prevent apps from making this unauthorized post to an announcement-only channel and bypassing this security control.
Slack should not trust third party apps to restrict who can post to an announcement-only channel. Doing so at present will require uninstalling many third party apps used by customers to prevent this vulnerability.
Impact
In this case #general was locked down because everyone was in it and kept posting @here comments that annoyed people. An attacker, however, could post a phishing message with a malicious link to a channel such as #general which all employees would see in their Slack.
A Workspace Owners/org admin must monitor the channel and delete unauthorized posts to mitigate.
An attacker can also quickly delete the Poll post to minimize the chance of a legit admin seeing the post and determining who was phished.
Vendor Response
The vendor states that these security bugs must be addressed in the third party apps themselves.Timeline
| Feb. 14, 2019 | Reported via Slack.com instructions to https://hackerone.com/reports/496095 |
| Feb. 18, 2019 | Vendor replies they will not fix. |
| Feb. 18, 2019 | Request to make report public |
| Mar. 20, 2019 | 30 day mark and public disclosure |
- Linux Guest will not Autoresize Display in VMWare Workstation Pro 25H2
- Network Adapter Disappears or No Media After Windows Resumes From Sleep
- NanoPi R76S as a Router Benchmarks
- AMD Gigabyte BIOS HD Audio Options
- Misc Useful Commands