I was not the one to report this or find this, but I did confirm the vulnerablity in the scan data zip download. The original release notes only mentioned "username-encrypted passwords" were disclosed.
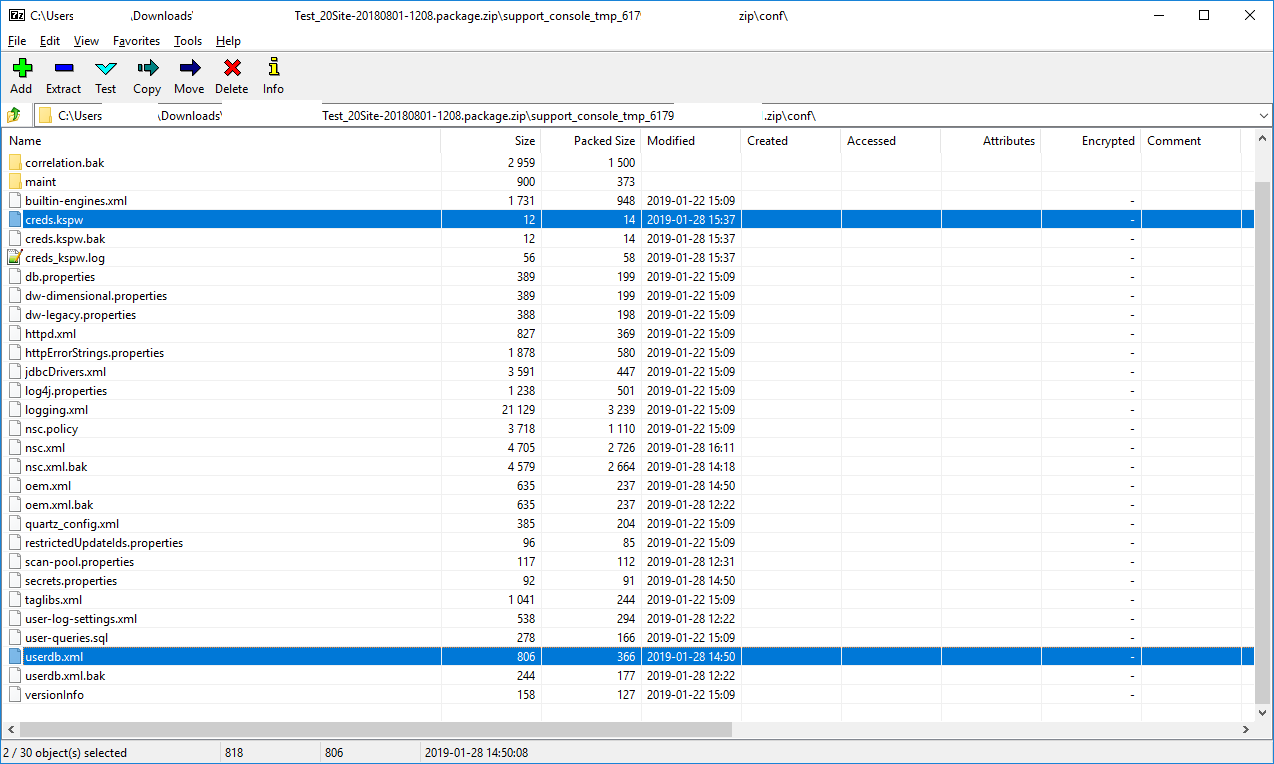
While reviewing I also noticed that the creds.kspw file was also being included. This file includes the clear-text password that is used when restoring a backup as well as for the Java keystore used internally by the product. The release notes did not mention this password leakage.
I contacted the vendor and asked for a way to change the keystore password. There is no official web UI or command-line tool, but the vendor support did provide a hidden web UI feature that was successful in changing this password. For all previous backup files the old password could not be changed so I recommend gpg encrypting those. For new ones going forward the new password is applied. Old backup files still require the old password of course.
I sent a note to the vulnerability reporting team at Rapid7, and they got the release notes updated to include that the clear-text password was also exposed. An attacker would need the password and an old backup file to obtain sensitive information.
The new release notes text as of March 11, 2019:
We fixed CVE-2019-5615, which allowed users with Site-level permissions to access files containing the username-encrypted passwords of Security Console Global Administrators and clear-text passwords for restoring backups, as well as the salt for those passwords. Valid credentials were required to access these files and malicious users would still have needed to perform additional work to decrypt the credentials and escalate their privileges. This issue affects Security Console versions 6.5.11 through 6.5.49. If your Security Console currently falls on or within this affected version range, ensure that you update your Security Console to the latest version.
https://help.rapid7.com/insightvm/en-us/release-notes/
- Linux Guest will not Autoresize Display in VMWare Workstation Pro 25H2
- Network Adapter Disappears or No Media After Windows Resumes From Sleep
- NanoPi R76S as a Router Benchmarks
- AMD Gigabyte BIOS HD Audio Options
- Misc Useful Commands