I received my new AT&T U-verse device, a 2WIRE 3600HGV. I was surprised at how big the thing is!

I noticed some interesting things about the default security settings:
- The default wireless encryption mode is WPA/WPA2 PSK with TKIP AND CCMP (AES)
- I prefer just WPA2 CCMP (AES), but this is much improved over a default of Open or WEP
- WPS is disabled be default which is a great benefit to avoid known vulnerabilities with it
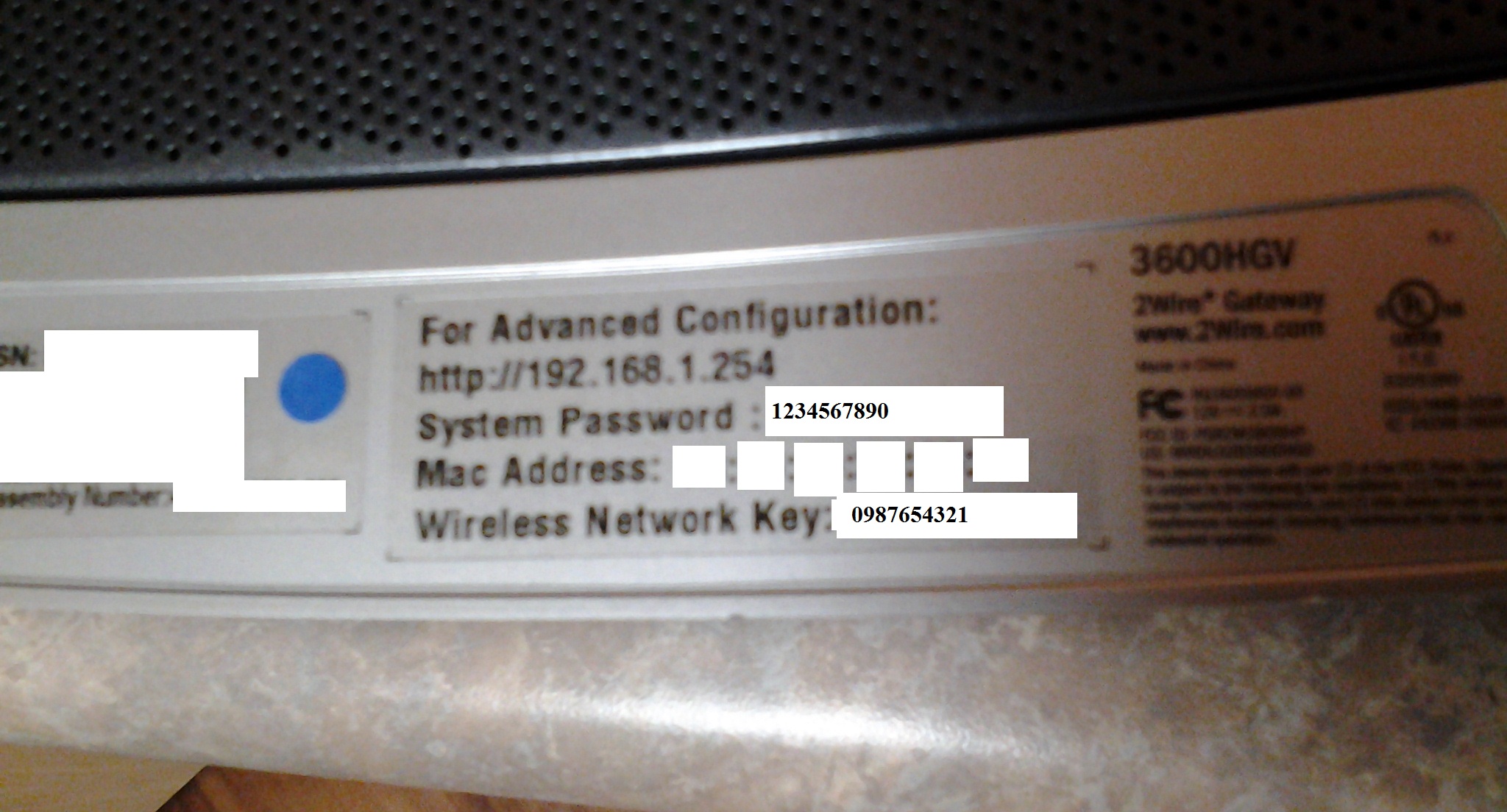
- The router admin password is random for each device
- BUT it only consists of ten characters with values of 0-9
- Resulting in only 10^10 combinations
- Granted to brute force you have to hit the web interface, but if you could get 1,000/sec it would take you around 116 days
- The wireless password is random for each device
- BUT it only consists of ten characters with values of 0-9 (again!)
- Resulting in only 10^10 combinations
- Using off-line brute force you can just capture some packets and go at this thing fast
- This script author claims to have a setup that can do 35,000 keys / second. That's just about 80 hours (~3.3 days) to brute force the wireless key on modest hardware
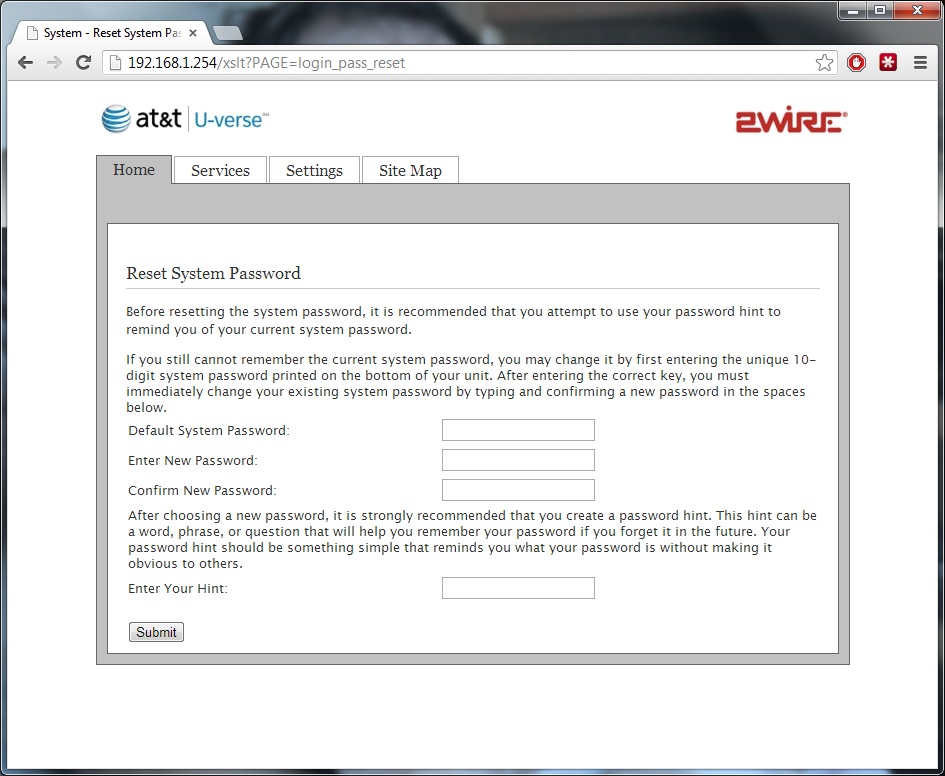
- The password reset mechanism for the admin part of the modem just requires the default admin key
- If someone saw the default password changing it would not help. They could always reset whatever you program remotely.
- It would have been better if they required the reset button to have been pressed and held down instead
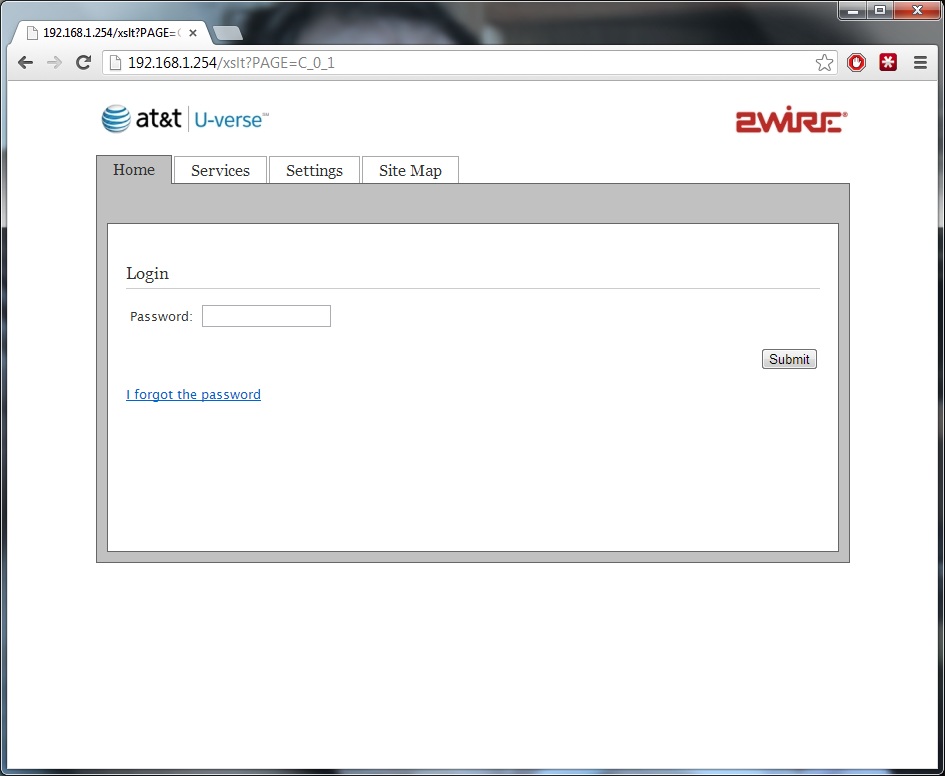
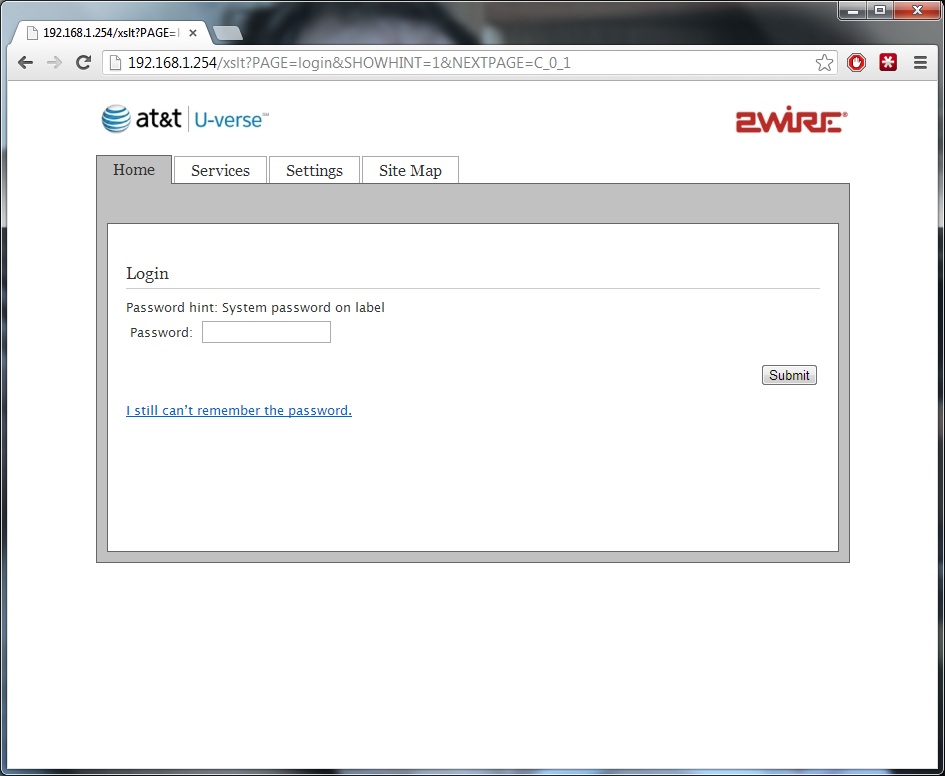
The forgot your password process:
- Linux Guest will not Autoresize Display in VMWare Workstation Pro 25H2
- Network Adapter Disappears or No Media After Windows Resumes From Sleep
- NanoPi R76S as a Router Benchmarks
- AMD Gigabyte BIOS HD Audio Options
- Misc Useful Commands